
Amazon has a service named KMS, Which is used to manage your keys, These keys can be used to encrypt/decrypt data encryption keys used to encrypt PHI or PII in customer applications.
Mentioned in the AWS HIPAA Compliance Whitepaper.
AWS KMS can be used in conjunction with a HIPAAaccount, but PHI may only be processed, stored, or transmitted in HIPAA-eligible services. KMS does not need to be a HIPAA-eligible service so long as it is used to generate and manage keys for applications running in other HIPAA-eligible services.
Recently i had a requirement in my project to encrypt PII, When it comes to HIPAA the data has to be encrypted in both in transit and in rest, the data in transit will be handled by https, so the data that been transmitted to and fro will be encrypted, what about the data that is in rest.
The data can be encrypted in the server side with a key, In Ruby there are several options to encrypt particular columns in the table with ActiveRecord and Mongo, few of them are
attr_encrypted, strongbox, crypt_keper and mongoid-encrypted-fields for mongoid
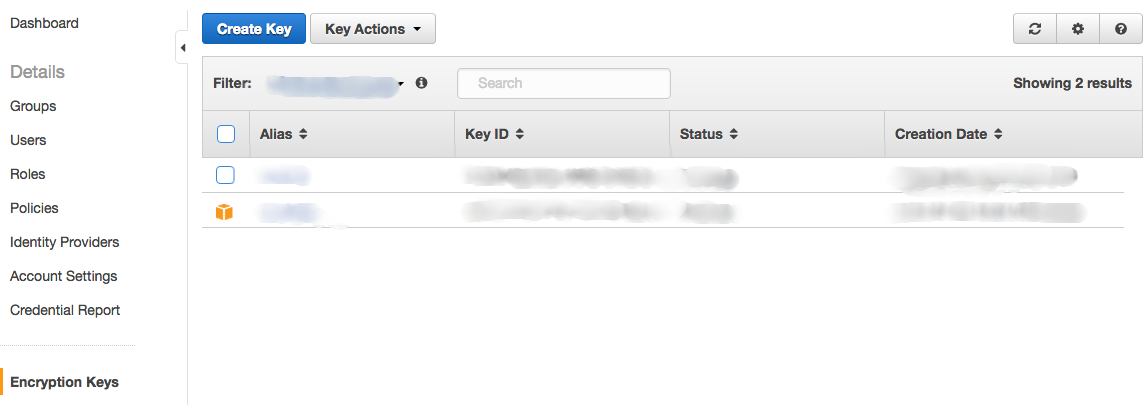
Navigate to IAM service where you will see options to manage users, groups, roles, polices and and option to encryption keys, create an encryption key.
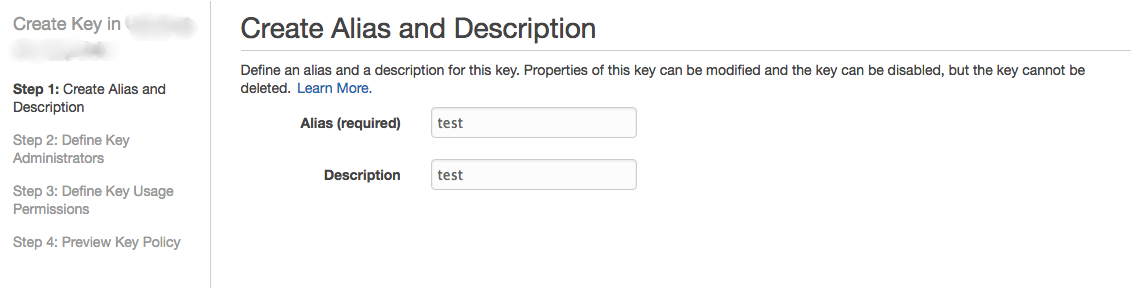
Click on create key to create a new key, enter name and description and cliek next.
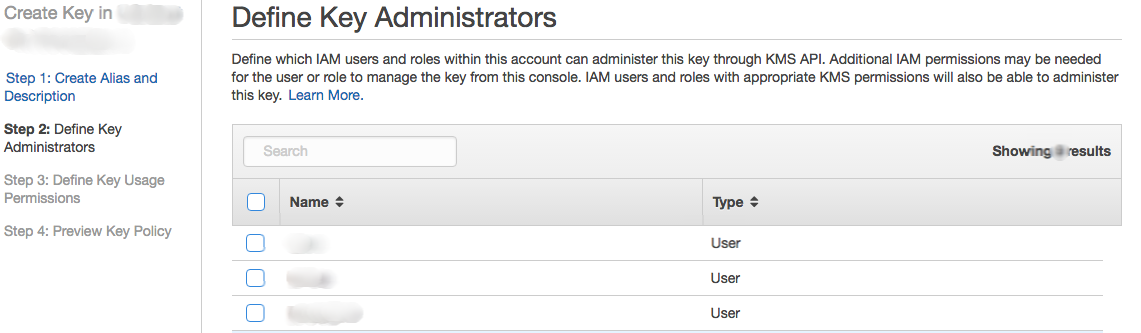
Define the administrator who can mange this key.
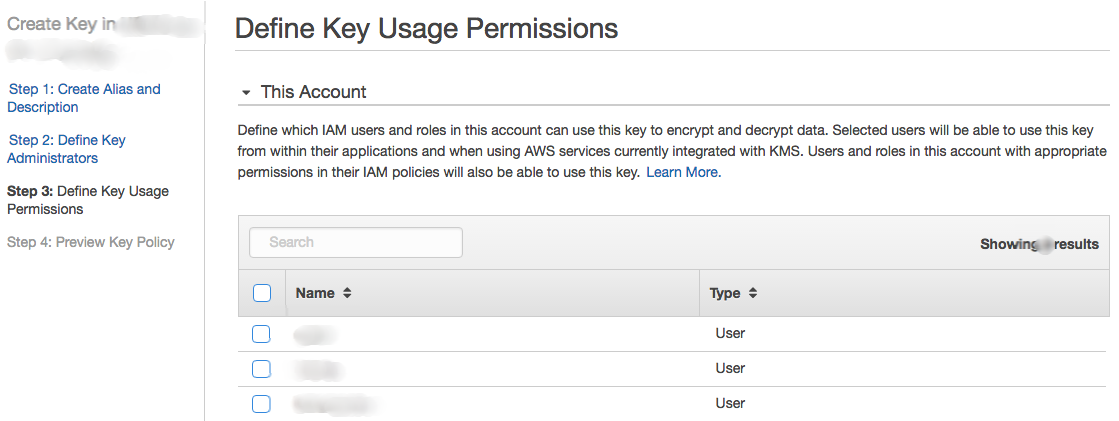
Next step is to define the key usage permission, check the users who can mange the key.
Finally you will see the preview of key policy, which will show the permissions and policies the key has with the user and group.
Once done, you will see the new key listing in your encryption keys list, your key will look something like this 1628ty4g-61mn-4695-8128-8fd690f34fad. In my next blog will explain how to make use of this key to encrypt data in a Rails application with the combination of some encryption gem.
